Quality of Service with Dynamic Multipoint VPN
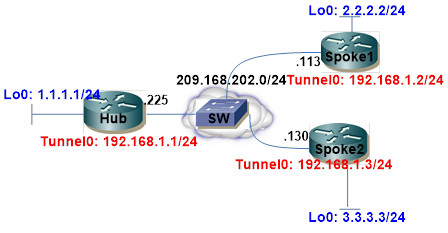
Cấu hình Router HUB
show run
Building configuration...
Current configuration : 2172 bytes
!
version 12.3
!
hostname Hub
!
enable password cisco
!
no aaa new-model
!
!
ip subnet-zero
!
ip cef
!
no ip domain lookup
!
no ftp-server write-enable
!
match access-group name internal
!
policy-map qos
class match-encrypt
bandwidth 128
!
crypto isakmp policy 10
hash md5
authentication pre-share
crypto isakmp key cisco123 address 0.0.0.0 0.0.0.0
no crypto isakmp ccm
!
crypto ipsec transform-set strong esp-3des esp-md5-hmac
!
crypto ipsec profile cisco
set security-association lifetime seconds 120
set transform-set strong
!
interface Tunnel0
ip address 192.168.1.1 255.255.255.0
no ip redirects
ip mtu 1440
ip nhrp authentication cisco123
ip nhrp map multicast dynamic
ip nhrp network-id 1
no ip split-horizon
qos pre-classify
tunnel source FastEthernet0/0
tunnel mode gre multipoint
tunnel key 0
tunnel protection ipsec profile cisco
!
interface Loopback0
ip address 1.1.1.1 255.255.255.0
!
interface FastEthernet0/0
ip address 209.168.202.225 255.255.255.0
duplex auto
speed auto
service-policy output qos
!
interface FastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
interface Serial0/2/0
no ip address
shutdown
clockrate 2000000
!
interface IDS-Sensor1/0
no ip address
shutdown
hold-queue 60 out
!
router eigrp 90
network 1.1.1.0 0.0.0.255
network 192.168.1.0
no auto-summary
!
ip classless
!
ip http server
no ip http secure-server
!
ip access-list extended internal
permit ip host 1.1.1.1 host 2.2.2.2
permit ip host 1.1.1.1 host 3.3.3.3
!
control-plane
!
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
end
Thực hiện show policy và debug trên HUB Router
Hub#show policy-map int fa0/0
FastEthernet0/0
Service-policy output: qos
Class-map: match-encrypt (match-all)
0 packets, 0 bytes
5 minute offered rate 0 bps, drop rate 0 bps
Match: access-group name internal
Queueing
Output Queue: Conversation 265
Bandwidth 128 (kbps) Max Threshold 64 (packets)
(pkts matched/bytes matched) 0/0
(depth/total drops/no-buffer drops) 0/0/0
Class-map: class-default (match-any)
1235 packets, 246725 bytes
5 minute offered rate 0 bps, drop rate 0 bps
Match: any
Hub#debug crypto engine
Crypto Engine debugging is on
Hub#
*Jun 25 04:56:00.171: CryptoEngine0: generate hmac context for conn id 1
*Jun 25 04:56:00.171: CryptoEngine0: validate proposal
*Jun 25 04:56:00.171: CryptoEngine0: validate proposal request
*Jun 25 04:56:00.171: CryptoEngine0: generate hmac context for conn id 1
*Jun 25 04:56:00.175: crypto_engine: ipsec_key_create_by_keys
*Jun 25 04:56:00.175: crypto_engine: ipsec_key_create_by_keys
*Jun 25 04:56:00.195: CryptoEngine0: generate hmac context for conn id 1
Hub#
*Jun 25 04:56:11.711: CryptoEngine0: generate hmac context for conn id 2
*Jun 25 04:56:11.983: CryptoEngine0: generate hmac context for conn id 2
*Jun 25 04:56:11.987: CryptoEngine0: validate proposal
*Jun 25 04:56:11.987: CryptoEngine0: validate proposal request
*Jun 25 04:56:11.987: CryptoEngine0: generate hmac context for conn id 2
*Jun 25 04:56:11.987: crypto_engine: ipsec_key_create_by_keys
*Jun 25 04:56:11.987: crypto_engine: ipsec_key_create_by_keys
Hub#
*Jun 25 04:56:30.195: crypto engine: deleting IPSec SA NETGX:4
*Jun 25 04:56:30.195: crypto_engine: IPSec SA delete
*Jun 25 04:56:30.195: crypto engine: deleting IPSec SA NETGX:12
*Jun 25 04:56:30.195: CryptoEngine0: generate hmac context for conn id 1
*Jun 25 04:56:30.195: crypto_engine: IPSec SA delete
Hub#debug crypto ipsec
Crypto IPSEC debugging is on
Hub#
*Jun 25 04:50:41.519: IPSEC(delete_sa): deleting SA,
(sa) sa_dest= 209.168.202.225, sa_proto= 50,
sa_spi= 0x384D6B73(944597875),
sa_trans= esp-3des esp-md5-hmac , sa_conn_id= 2011,
(identity) local= 209.168.202.225, remote= 209.168.202.131,
local_proxy= 209.168.202.225/255.255.255.255/47/0 (type=1),
remote_proxy= 209.168.202.131/255.255.255.255/47/0 (type=1)
*Jun 25 04:50:41.519: IPSEC(delete_sa): deleting SA,
(sa) sa_dest= 209.168.202.131, sa_proto= 50,
sa_spi= 0x33345E4D(859070029),
sa_trans= esp-3des esp-md5-hmac , sa_conn_id= 2001,
(identity)
Hub#
local= 209.168.202.225, remote= 209.168.202.131,
local_proxy= 209.168.202.225/255.255.255.255/47/0 (type=1),
remote_proxy= 209.168.202.131/255.255.255.255/47/0 (type=1)
*Jun 25 04:50:41.519: IPSec: Flow_switching Deallocated flow for sibling 80000056
Hub#
*Jun 25 04:50:51.187: IPSEC(key_engine): got a queue event with 1 kei messages
*Jun 25 04:50:51.187: IPSEC(key_engine_delete_sas): rec'd delete notify from ISA
KMP
*Jun 25 04:50:51.187: IPSEC(key_engine_delete_sas): delete SA with spi 0xC606512
8 proto 50 for 209.168.202.130
*Jun 25 04:50:51.187: IPSEC(delete_sa): deleting SA,
(sa) sa_dest= 209.168.202.225, sa_proto= 50,
sa_spi= 0xB00657AE(2953205678),
sa_trans= esp-3des esp-md5-hmac , sa_conn_id= 2006,
(identity) local= 209.168.202.225, remote= 209.168.202.130,
local_proxy= 209.168.202.225/255.255.255.255/47/0 (type=1),
remote_proxy= 209.168.202.130/255.255.255.255/47/0 (type=1)
Hub#
*Jun 25 04:50:51.187: IPSEC(delete_sa): deleting SA,
(sa) sa_dest= 209.168.202.130, sa_proto= 50,
sa_spi= 0xC6065128(3322302760),
sa_trans= esp-3des esp-md5-hmac , sa_conn_id= 2005,
(identity) local= 209.168.202.225, remote= 209.168.202.130,
local_proxy= 209.168.202.225/255.255.255.255/47/0 (type=1),
remote_proxy= 209.168.202.130/255.255.255.255/47/0 (type=1)
*Jun 25 04:50:51.187: IPSec: Flow_switching Deallocated flow for sibling 80000057
Hub#debug crypto isakmp
Crypto ISAKMP debugging is on
Hub#
*Jun 25 04:53:37.155: ISAKMP: Unlocking IPSEC struct 0x463EDFDC from delete_siblings, count 1
*Jun 25 04:53:37.155: ISAKMP: received ke message (3/1)
*Jun 25 04:53:37.155: ISAKMP: set new node -1349345391 to QM_IDLE
*Jun 25 04:53:37.155: ISAKMP:(0:1:SW:1): sending packet to 209.168.202.131 my_port 500 peer_port 500 (R) QM_IDLE
*Jun 25 04:53:37.155: ISAKMP:(0:1:SW:1):purging node -1349345391
*Jun 25 04:53:37.155: ISAKMP:(0:1:SW:1):Input = IKE_MESG_FROM_IPSEC, IKE_PHASE2_DEL
*Jun 25 04:53:37.159: ISAKMP:(0:1:SW:1):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
Hub#
*Jun 25 04:53:49.167: ISAKMP: Unlocking IPSEC struct 0x459C9114 from delete_siblings, count 3
*Jun 25 04:53:49.167: ISAKMP: received ke message (3/1)
*Jun 25 04:53:49.167: ISAKMP: set new node -1141056925 to QM_IDLE
*Jun 25 04:53:49.167: ISAKMP:(0:2:SW:1): sending packet to 209.168.202.130 my_port 500 peer_port 500 (R) QM_IDLE
*Jun 25 04:53:49.167: ISAKMP:(0:2:SW:1):purging node -1141056925
*Jun 25 04:53:49.167: ISAKMP:(0:2:SW:1):Input = IKE_MESG_FROM_IPSEC, IKE_PHASE2_DEL
*Jun 25 04:53:49.167: ISAKMP:(0:2:SW:1):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
Hub#
*Jun 25 04:53:49.359: ISAKMP (0:134217730): received packet from 209.168.202.130 dport 500 sport 500 Global (R) QM_IDLE
*Jun 25 04:53:49.363: ISAKMP: set new node -1206626322 to QM_IDLE
*Jun 25 04:53:49.363: ISAKMP:(0:2:SW:1): processing HASH payload. message ID = -1206626322
*Jun 25 04:53:49.363: ISAKMP:(0:2:SW:1): processing DELETE payload. message ID = -1206626322
*Jun 25 04:53:49.363: ISAKMP:(0:2:SW:1):peer does not do paranoid keepalives.
*Jun 25 04:53:49.363: ISAKMP:(0:2:SW:1):deleting node -1206626322 error FALSE reason "Informational (in) state 1"
*Jun 25 04:53:49.363: ISAKMP: Unlocking IPSEC struct 0x459C9114 from delete_siblings, count 2
Hub#
*Jun 25 04:53:57.155: ISAKMP:(0:1:SW:1):purging node -1528999289
Hub#
*Jun 25 04:54:07.923: ISAKMP:(0:2:SW:1):purging node 1187545819
*Jun 25 04:54:07.983: ISAKMP:(0:2:SW:1):purging node -1480648805
Hub#u all
*Jun 25 04:54:32.691: ISAKMP (0:134217729): received packet from 209.168.202.131 dport 500 sport 500 Global (R) QM_IDLE
*Jun 25 04:54:32.691: ISAKMP: set new node -507463311 to QM_IDLE
*Jun 25 04:54:32.695: ISAKMP:(0:1:SW:1): processing HASH payload. message ID = -507463311
*Jun 25 04:54:32.695: ISAKMP:(0:1:SW:1): processing SA payload. message ID = -507463311
*Jun 25 04:54:32.695: ISAKMP:(0:1:SW:1):Checking IPSec proposal 1
*Jun 25 04:54:32.695: ISAKMP: transform 1, ESP_3DES
*Jun 25 04:54:32.695: ISAKMP: attributes in transform:
*Jun 25 04:54:32.695: ISAKMP: encaps is 1 (Tunnel)
*Jun 25 04:54:32.695: ISAKMP: SA life type in seconds
*Jun 25 04:54:32.695: ISAKMP: SA life duration (basic) of 120
*Jun 25 04:54:32.695: ISAKMP: SA life type in kilobytes
*Jun 25 04:54:32.695: ISAKMP: SA life duration (VPI) of 0x0 0x46 0x50 0x0
*Jun 25 04:54:32.695: ISAKMP: authenticator is HMAC-MD5
*Jun 25 04:54:32.695: ISAKMP:(0:1:SW:1):atts are
Cấu hình Router Spoke 1
show run
Building configuration...
Current configuration : 1725 bytes
!
version 12.3
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Spoke1
!
boot-start-marker
boot-end-marker
!
enable password cisco
!
no aaa new-model
ip subnet-zero
ip cef
!
no ip domain lookup
!
ip audit po max-events 100
!
class-map match-all match-encrypt
match access-group name internal
!
policy-map qos
class match-encrypt
bandwidth 128
!
crypto isakmp policy 10
hash md5
authentication pre-share
crypto isakmp key cisco123 address 0.0.0.0 0.0.0.0
!
crypto ipsec transform-set strong esp-3des esp-md5-hmac
!
crypto ipsec profile cisco
set security-association lifetime seconds 120
set transform-set strong
!
interface Loopback0
ip address 2.2.2.2 255.255.255.0
!
interface Tunnel0
ip address 192.168.1.2 255.255.255.0
ip mtu 1440
ip nhrp authentication cisco123
ip nhrp map multicast dynamic
ip nhrp map 192.168.1.1 209.168.202.225
ip nhrp map multicast 209.168.202.225
ip nhrp network-id 1
ip nhrp nhs 192.168.1.1
no ip split-horizon
qos pre-classify
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel key 0
tunnel protection ipsec profile cisco
!
interface Ethernet0/0
ip address 209.168.202.131 255.255.255.0
half-duplex
service-policy output qos
!
router eigrp 90
network 2.2.2.0 0.0.0.255
network 192.168.1.0
!
ip http server
no ip http secure-server
ip classless
ip route 0.0.0.0 0.0.0.0 209.168.202.225
ip route 3.3.3.0 255.255.255.0 Tunnel0
!
ip access-list extended internal
permit ip host 2.2.2.2 host 3.3.3.3
!
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
line vty 0 4
Spoke1#show policy-map interface e0/0
Ethernet0/0
Service-policy output: qos
Class-map: match-encrypt (match-all)
1150 packets, 251700 bytes
5 minute offered rate 0 bps, drop rate 0 bps
Match: access-group name internal
Queueing
Output Queue: Conversation 265
Bandwidth 128 (kbps) Max Threshold 64 (packets)
(pkts matched/bytes matched) 1150/251700
(depth/total drops/no-buffer drops) 0/0/0
Class-map: class-default (match-any)
1057 packets, 143746 bytes
5 minute offered rate 0 bps, drop rate 0 bps
Match: any
Cấu hình Router Spoke 2
show run
Building configuration...
Current configuration : 1805 bytes
!
version 12.3
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Spoke2
!
boot-start-marker
boot-end-marker
!
enable password cisco
!
no aaa new-model
ip subnet-zero
ip cef
!
no ip domain lookup
!
ip audit po max-events 100
!
class-map match-all match-encrypt
match access-group name internal
!
policy-map qos
class match-encrypt
bandwidth 128
!
crypto isakmp policy 10
hash md5
authentication pre-share
crypto isakmp key cisco123 address 0.0.0.0 0.0.0.0
!
crypto ipsec transform-set strong esp-3des esp-md5-hmac
!
crypto ipsec profile cisco
set security-association lifetime seconds 120
set transform-set strong
!
interface Loopback0
ip address 3.3.3.3 255.255.255.0
!
interface Tunnel0
ip address 192.168.1.3 255.255.255.0
ip mtu 1440
ip nhrp authentication cisco123
ip nhrp map multicast dynamic
ip nhrp map 192.168.1.1 209.168.202.225
ip nhrp map multicast 209.168.202.225
ip nhrp network-id 1
ip nhrp nhs 192.168.1.1
no ip split-horizon
qos pre-classify
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel key 0
tunnel protection ipsec profile cisco
!
interface Ethernet0/0
ip address 209.168.202.130 255.255.255.0
half-duplex
service-policy output qos
!
router eigrp 90
network 3.3.3.0 0.0.0.255
network 192.168.1.0
!
ip http server
no ip http secure-server
ip classless
ip route 0.0.0.0 0.0.0.0 209.168.202.225
ip route 2.2.2.0 255.255.255.0 Tunnel0
!
ip access-list extended internal
permit ip host 3.3.3.3 host 2.2.2.2
end
Thông tin khác
- » Configuring a Router IPSec Tunnel Private-to-Private Network with NAT and a Static (01.06.2023)
- » LỊCH KHAI GIẢNG THÁNG 6/2023 (31.05.2023)
- » Configuring Dynamic Multipoint VPN (DMVPN) using GRE over IPSec between Multiple Routers (31.05.2023)
- » TỔNG KHAI GIẢNG CÁC LỚP CCNA – CCNA ONLINE – CCNP ENCOR TẠI VNPRO (30.05.2023)
- » BẾ GIẢNG LỚP CCNA 23A02 (30.05.2023)
- » BẾ GIẢNG LỚP CCNA 23A05 (27.05.2023)
- » VPN Backup using IPSEC-DPD (25.05.2023)
- » EZVPN – Server using SDM (24.05.2023)





