LAB 15: Dùng uRPF để chống IP Address Spoofing
Mục tiêu
Cấu hình router dùng uRPF để chống IP Address Spoofing
Hình vẽ
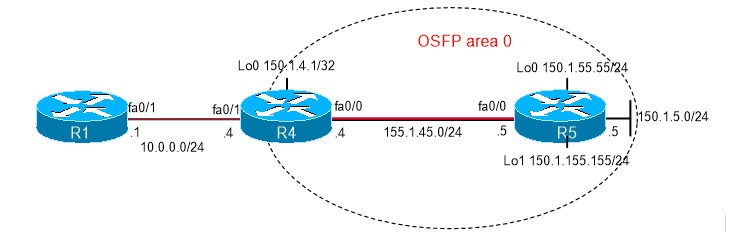
Mô tả
- Cấu hình “static NAT”
- Bật tính năng kiểm tra uRPF, bỏ qua không kiểm tra 1 vài networks.
- Tất cả các IP spoofing sẽ bị log lại
- Tạo 2 interface loopback: lo0 có IP address là 150.1.55.55/24 và lo1 150.1.155.155/24
- Không quảng bá 2 loopback này vào giao thức định tuyến đang chạy
- Tạo ACL 100 trên Router 4, permit mạng 150.1.55.0/24. Deny và log các traffic còn lại.
- Cấu hình uRPF trên interface fa0/0 của Router 4. Apply acl 100 vào uRPF acl.
Cấu hình tham khảo
Bước 1: Cấu hình địa chỉ IP, định tuyến, Static NAT
Router 4
!
interface Loopback0
ip address 150.1.4.4 255.255.255.0
ip ospf network point-to-point
!
interface FastEthernet0/0
ip address 155.1.45.4 255.255.255.0
ip nat outside
ip virtual-reassembly
speed auto
!
interface FastEthernet0/1
ip address 10.0.0.4 255.255.255.0
ip nat inside
ip virtual-reassembly
speed auto
!
router ospf 1
log-adjacency-changes
network 150.1.4.0 0.0.0.255 area 0
network 155.1.45.0 0.0.0.255 area 0
!
ip classless
!
ip nat inside source static 10.0.0.1 interface Loopback0
!
Router 5
!
interface Loopback0
ip address 150.1.55.55 255.255.255.0
!
interface Loopback1
ip address 150.1.155.155 255.255.255.0
!
interface FastEthernet0/0
ip address 155.1.45.5 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet0/0
ip address 155.1.45.5 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 150.1.5.5 255.255.255.0
duplex auto
speed auto
no keepalive
!
router ospf 1
log-adjacency-changes
network 150.1.5.0 0.0.0.255 area 0
network 155.1.45.0 0.0.0.255 area 0
!
Router 1
!
interface FastEthernet0/0
ip address 10.0.0.1 255.255.255.0
duplex auto
speed auto
!
ip classless
ip route 0.0.0.0 0.0.0.0 10.0.0.4
!
Bước 2: Cấu hình uRPF trên Router 4
Router 4
!
ip cef
!
interface FastEthernet0/0
ip verify unicast reverse-path 100
!
access-list 100 permit ip 150.1.55.0 0.0.0.255 any
access-list 100 deny ip any any log
!
Lưu ý:
- Để tính năng uRPF được thực hiện thì CEF phải được enaled trên router.
- Trước tiên uRPF sẽ xác định gói tin có bị spoofed hay không. Nếu đó là một packets bị spoofed thì sẽ dựa vào ACL để xác định hành động tiếp theo đối với gói tin đó. Nếu trong ACL permit thì spoofed packet sẽ được cho phép, deny sẽ drop spoofed packet.
- Trong trường hợp không có ACL thì uRPF sẽ tự động drop packets mà nó nghi ngờ là đã bị spoofed
Bước 3: Kiểm tra.
Router 5
R5#ping 150.1.4.4 source loopback 0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 150.1.4.4, timeout is 2 seconds:
Packet sent with a source address of 150.1.55.55
.....
Success rate is 0 percent (0/5)
Router 4
R4#show ip access-lists
Extended IP access list 100
10 permit ip 150.1.55.0 0.0.0.255 any (5 matches)
20 deny ip any any log
R4#show ip int fa0/0
FastEthernet0/0 is up, line protocol is up
Internet address is 155.1.45.4/24
Broadcast address is 255.255.255.255
<-- output omitted-->
IP verify source reachable-via RX, allow default, ACL 100
5 verification drops
20 suppressed verification drops
R4#
Lưu ý:
packet đến từ R5, trước tiên uRPF kiểm tra và cho rằng đây là spoofed packet, trong ACL 100 permit mạng 150.1.55.0/24 nên spoofed packet vẫn được cho qua. Tuy nhiên vì không có route 150.1.55.0/24 trong routing table nên R4 không biết đường trả về gói echo-reply.
Router 5
R5#ping 150.1.4.4 source loopback 1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 150.1.4.4, timeout is 2 seconds:
Packet sent with a source address of 150.1.155.155
.....
Success rate is 0 percent (0/5)
Router 4
R4#
*Jun 5 09:45:08.255: %SEC-6-IPACCESSLOGDP: list 100 denied icmp 150.1.155.155 -> 150.1.4.4 (0/0), 2 packets
R4#show ip access-lists
Extended IP access list 100
10 permit ip 150.1.55.0 0.0.0.255 any (5 matches)
20 deny ip any any log (5 matches)
R4#show ip int fa0/0
FastEthernet0/0 is up, line protocol is up
Internet address is 155.1.45.4/24
Broadcast address is 255.255.255.255
<-- output omitted-->
IP verify source reachable-via RX, allow default, ACL 100
10 verification drops
20 suppressed verification drops
R4#show cef int fa0/0
FastEthernet0/0 is up (if_number 4)
Corresponding hwidb fast_if_number 4
<-- output omitted-->
IP unicast RPF check is enabled
Inbound access list is not set
<-- output omitted-->
Lưu ý:
packet đến từ R5, trước tiên uRPF kiểm tra và cho rằng đây là spoofed packet, trong ACL 100 chỉ permit mạng 150.1.55.0/24 và deny tất cả nên spoofed packet bị drop.
Thông tin khác
- » ĐĂNG KÝ THAM GIA LỚP ĐÀO TẠO GIẢNG VIÊN CCNA THÁNG 7 TẠI TRUNG TÂM TIN HỌC VNPRO (10.07.2023)
- » LAB 14: Chống IP Address Spoofing bằng ACLs (05.07.2023)
- » TI GROUP TUYỂN THỰC TẬP SINH NGÀNH QUẢN TRỊ MẠNG (05.07.2023)
- » VNPRO HÂN HẠNH PHÁT HÀNH BẢN TIN DANCISCO THÁNG 07/2023 (04.07.2023)
- » LAB 13: Dùng CAR để hạn chế Smurf Attack (03.07.2023)
- » VnPro xin chúc mừng các anh/chị học viên thi đậu chứng chỉ quốc tế CCNP SD-WAN (01.07.2023)
- » BẾ GIẢNG LỚP CCNA 23A06 (01.07.2023)
- » LAB 12: Cấu hình Application Port-Mapping với CBAC (30.06.2023)





