CHƯƠNG 1 : TỔNG QUÁT HOẠT ĐỘNG VÀ CẤU HÌNH CƠ BẢN THIẾT BỊ ASA - Phần 2
LAB 1.3: THỰC HIỆN NAT ĐỘNG VÀ PAT
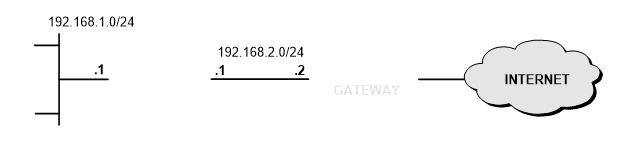
Hình 1.28
1. Mô tả
Cho phép truy cập dịch vụ bên ngoài Internet từ mạng 192.168.1.0/24 với yêu cầu:
- Dãy địa chỉ từ 192.168.1.1-182.168.1.127 sẽ Nat động tương ứng với dãy địa chỉ 192.168.2.10-192.168.2.100.
- Dãy địa chỉ từ 192.168.1.128-192.168.1.254 sẽ PAT tương ứng với địa chỉ 192.168.2.9.
2. Cấu hình
Xác định dãy địa chỉ thứ nhất:
ASA(config)# nat (inside) 1 192.168.1.0 255.255.255.128
Xác định dãy địa chỉ thứ hai:
ASA(config)# nat (inside) 2 192.168.1.128 255.255.255.128
Thực hiện NAT động cho dãy địa chỉ thứ nhất:
ASA(config)# global (outside) 1 192.168.2.10-192.168.2.100 netmask 255.255.255.0
Thực hiện PAT cho dãy địa chỉ thứ hai:
ASA(config)# global (outside) 2 192.168.2.9 netmask 255.255.255.0
3. Cấu hình đầy đủ
ASA
ASA Version 8.0(2)
!
hostname ASA
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0/0
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet0/1
nameif outside
security-level 0
ip address 192.168.2.1 255.255.255.0
!
interface Ethernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
shutdown
no nameif
no security-level
no ip address
management-only
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
access-list PING extended permit icmp any any echo-reply
global (outside) 1 192.168.2.10-192.168.2.100 netmask 255.255.255.0
global (outside) 2 192.168.2.9 netmask 255.255.255.0
nat (inside) 1 192.168.1.0 255.255.255.128
nat (inside) 2 192.168.1.128 255.255.255.128
access-group PING in interface outside
route outside 0.0.0.0 0.0.0.0 192.168.2.2 1
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:dba2db98f02aa720ff5cea67b371a558
: end
GATEWAY
Building configuration...
Current configuration : 726 bytes
hostname GATEWAY
!
interface FastEthernet0/0
ip address 192.168.2.2 255.255.255.0
ip nat inside
duplex auto
speed auto
!
interface FastEthernet0/1
ip address dhcp
ip nat outside
duplex auto
speed auto
!
ip nat inside source list 1 interface FastEthernet0/1 overload
ip classless
ip http server
no ip http secure-server
!
access-list 1 permit 192.168.2.0 0.0.0.255
!
line vty 0 4
login
!
end
4. Kiểm tra
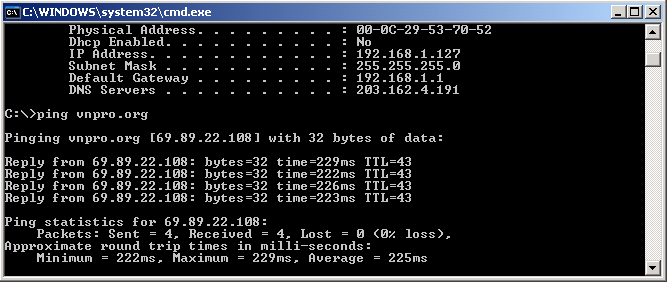
Thực hiện kiểm tra dùng ping với PC có địa chỉ thuộc dãy thứ nhất (hình 1.29).
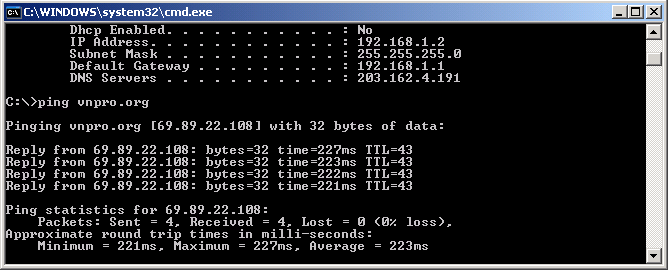
Hình 1.29
ASA(config)# sh xlate
1 in use, 8 most used
Global 192.168.2.10 Local 192.168.1.2
ASA(config)# sh xlate
2 in use, 8 most used
Global 192.168.2.10 Local 192.168.1.2
Global 192.168.2.11 Local 192.168.1.127
Hình 1.30
Thực hiện truy cập dùng ping với PC có địa chỉ thuộc dãy thứ hai (hình 1.31).
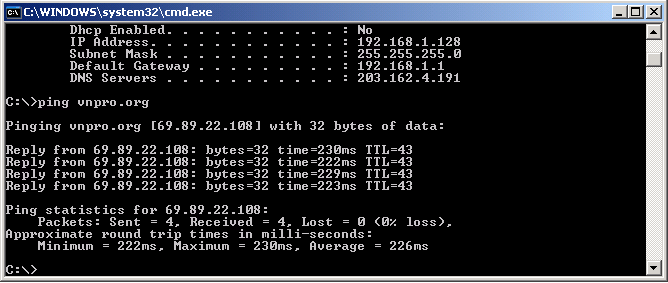
Hình 1.31
ASA(config)# sh xlate
6 in use, 8 most used
Global 192.168.2.10 Local 192.168.1.2
PAT Global 192.168.2.9(1) Local 192.168.1.128 ICMP id 512
PAT Global 192.168.2.9(1025) Local 192.168.1.128(1110)
PAT Global 192.168.2.9(1) Local 192.168.1.128(123)
PAT Global 192.168.2.9(1024) Local 192.168.1.128(1054)
Global 192.168.2.11 Local 192.168.1.127
LAB 1.4: THỰC HIỆN NAT VÀ PAT THEO CHÍNH SÁCH
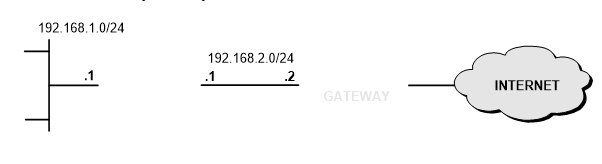
Hình 1.32
1. Mô tả
Cho phép truy cập dịch vụ ngoài Internet với yêu cầu:
- Lưu lượng thuộc mạng 192.168.1.0/24 là tcp hoặc udp sẽ được NAT tương ứng với dãy địa chỉ 192.168.2.10-192.168.2.100.
- Lưu lượng thuộc mạng 192.168.1.0/24 là icmp sẽ được PAT tương ứng địa chỉ 192.168.2.9.
2. Cấu hình
Xác định luồng dữ liệu được NAT:
ASA(config)# access-list POLICY_NAT permit tcp 192.168.1.0 255.255.255.0 any
ASA(config)# access-list POLICY_NAT permit udp 192.168.1.0 255.255.255.0 any
Xác định luồng dữ liệu được PAT:
ASA(config)# access-list POLICY_PAT permit icmp 192.168.1.0 255.255.255.0 any
Thực hiện NAT:
ASA(config)# nat (inside) 1 access-list POLICY_NAT
ASA(config)# global (outside) 1 192.168.2.10-192.168.2.100 netmask 255.255.255.0
Thực hiện PAT:
ASA(config)# nat (inside) 2 access-list POLICY_PAT
ASA(config)# global (outside) 2 192.168.2.9
3. Cấu hình đầy đủ
ASA
ASA Version 8.0(2)
!
hostname ASA
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0/0
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet0/1
nameif outside
security-level 0
ip address 192.168.2.1 255.255.255.0
!
interface Ethernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
shutdown
no nameif
no security-level
no ip address
management-only
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
access-list PING extended permit icmp any any echo-reply
access-list POLICY_NAT extended permit tcp 192.168.1.0 255.255.255.0 any
access-list POLICY_NAT extended permit udp 192.168.1.0 255.255.255.0 any
access-list POLICY_PAT extended permit icmp 192.168.1.0 255.255.255.0 any
global (outside) 1 192.168.2.10-192.168.2.100 netmask 255.255.255.0
global (outside) 2 192.168.2.9
nat (inside) 1 access-list POLICY_NAT
nat (inside) 2 access-list POLICY_PAT
access-group PING in interface outside
route outside 0.0.0.0 0.0.0.0 192.168.2.2 1
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:dba2db98f02aa720ff5cea67b371a558
: end
GATEWAY
Building configuration...
Current configuration : 726 bytes
hostname GATEWAY
!
interface FastEthernet0/0
ip address 192.168.2.2 255.255.255.0
ip nat inside
duplex auto
speed auto
!
interface FastEthernet0/1
ip address dhcp
ip nat outside
duplex auto
speed auto
!
ip nat inside source list 1 interface FastEthernet0/1 overload
ip classless
ip http server
!
access-list 1 permit 192.168.2.0 0.0.0.255
!
line vty 0 4
login
!
end
4. Kiểm tra
Thực hiện truy cập dịch vụ Web (hình 1.33).
ASA(config)# sh xlate
1 in use, 8 most used
Global 192.168.2.11 Local 192.168.1.2
Hình 1.33
Thực hiện ping vnpro.org (hình 1.34).
Hình 1.34
ASA(config)# sh xlate
2 in use, 8 most used
PAT Global 192.168.2.9(2) Local 192.168.1.2 ICMP id 512
Global 192.168.2.11 Local 192.168.1.2
LAB 1.5: THỰC HIỆN NAT TĨNH
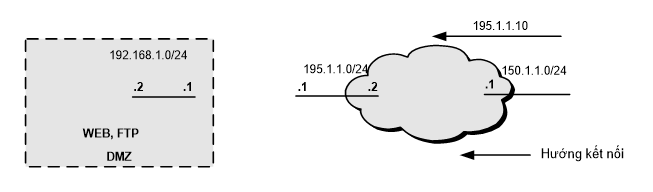
Hình 1.35
1. Mô tả
Cho phép người dùng từ bên ngoài có thể truy cập dịch vụ Web và FTP trong DMZ với địa chỉ 195.1.1.10 dùng Nat tĩnh.
2. Cấu hình
Định nghĩa thông tin cổng DMZ:
ASA(config)# interface e0/0
ASA(config-if)# ip address 192.168.1.1 255.255.255.0
ASA(config-if)# nameif DMZ
ASA(config-if)# security-level 50
ASA(config-if)# no shut
Định nghĩa thông tin cổng outside:
ASA(config)# interface e0/1
ASA(config-if)# ip address 195.1.1.1 255.255.255.0
ASA(config-if)# nameif outside
INFO: Security level for "outside" set to 0 by default.
Thực hiện NAT tĩnh từ địa chỉ 192.168.1.2->195.1.1.10:
ASA(config)# static (DMZ,outside) 195.1.1.10 192.168.1.2
Xác định chính sách để cho truy cập dịch vụ trong vùng DMZ:
ASA(config)# access-list POLICY permit tcp any host 195.1.1.10 eq 21
ASA(config)# access-list POLICY permit tcp any host 195.1.1.10 eq 80
ASA(config)# access-group POLICY in interface outside
3. Cấu hình đầy đủ
ASA
ASA Version 8.0(2)
!
hostname ASA
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0/0
nameif DMZ
security-level 50
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet0/1
nameif outside
security-level 0
ip address 195.1.1.1 255.255.255.0
!
interface Ethernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
shutdown
no nameif
no security-level
no ip address
management-only
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
access-list POLICY extended permit tcp any host 195.1.1.10 eq ftp
access-list POLICY extended permit tcp any host 195.1.1.10 eq www
static (DMZ,outside) 195.1.1.10 192.168.1.2 netmask 255.255.255.255
access-group POLICY in interface outside
route outside 0.0.0.0 0.0.0.0 195.1.1.2 1
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:dba2db98f02aa720ff5cea67b371a558
: end
4. Kiểm tra
Trạng thái bảng NAT:
ASA(config)# sh xlate
1 in use, 1 most used
Global 195.1.1.10 Local 192.168.1.2
Truy cập dịch vụ Web trong DMZ (hình 1.36).
Hình 1.36
Truy cập dịch vụ FTP trong DMZ (hình 1.37).
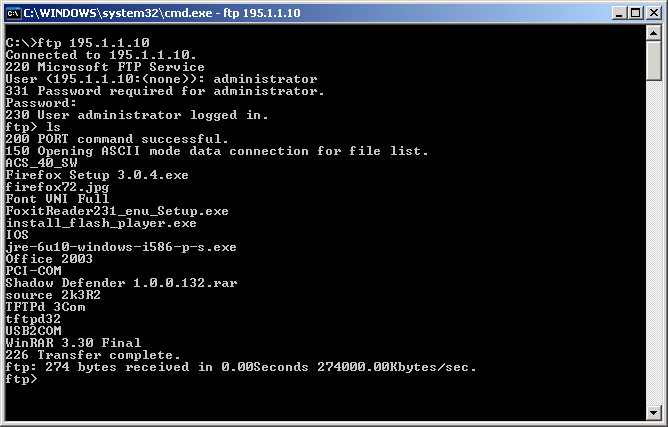
Hình 1.37
ASA(config)# sh conn
2 in use, 2 most used
TCP out 150.1.1.1:1062 in 192.168.1.2:80 idle 0:00:02 bytes 1055 flags UIOB
TCP out 150.1.1.1:1059 in 192.168.1.2:21 idle 0:01:13 bytes 273 flags UIOB
ASA(config)# sh access-list
access-list cached ACL log flows: total 0, denied 0 (deny-flow-max 4096)
alert-interval 300
access-list POLICY; 2 elements
access-list POLICY line 1 extended permit tcp any host 195.1.1.10 eq ftp (hitcnt=2) 0xd21b0663
access-list POLICY line 2 extended permit tcp any host 195.1.1.10 eq www (hitcnt=2) 0xa725c0b2
LAB 1.6: THỰC HIỆN NAT TĨNH CHO SUBNET
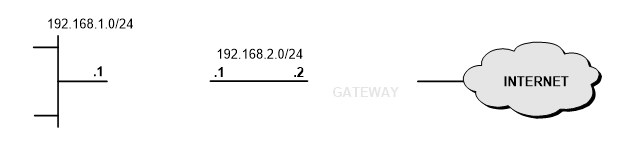
Hình 1.38
1. Mô tả
Cho phép truy cập dịch vụ ngoài Internet đảm bảo mạng 192.168.1.0/24 sẽ được NAT tĩnh tương ứng mạng 195.1.1.0/24.
2. Cấu hình
Thực hiện NAt tĩnh tương ứng từ mạng 192.168.1.0->195.1.1.0:
ASA(config)# static (inside,outside) 195.1.1.0 192.168.1.0 netmask 255.255.255.0
3. Cấu hình đầy đủ
GATEWAY
Building configuration...
Current configuration : 769 bytes
!
hostname GATEWAY
!
interface FastEthernet0/0
ip address 192.168.2.2 255.255.255.0
ip nat inside
duplex auto
speed auto
!
interface FastEthernet0/1
ip address dhcp
ip nat outside
duplex auto
speed auto
!
ip nat inside source list 1 interface FastEthernet0/1 overload
ip classless
ip route 195.1.1.0 255.255.255.0 192.168.2.1
ip http server
no ip http secure-server
!
access-list 1 permit 195.1.1.0 0.0.0.255
!
!
end
ASA
ASA Version 8.0(2)
!
hostname ASA
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0/0
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet0/1
nameif outside
security-level 0
ip address 192.168.2.1 255.255.255.0
!
interface Ethernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
shutdown
no nameif
no security-level
no ip address
management-only
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
access-list PING extended permit icmp any any echo-reply
static (inside,outside) 195.1.1.0 192.168.1.0 netmask 255.255.255.0
access-group PING in interface outside
route outside 0.0.0.0 0.0.0.0 192.168.2.2 1
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:dba2db98f02aa720ff5cea67b371a558
: end
4. Kiểm tra
Thực hiện truy cập dịch vụ Web (hình 1.39).

Hình 1.39
Thực hiện ping vnpro.org (hình 1.40).
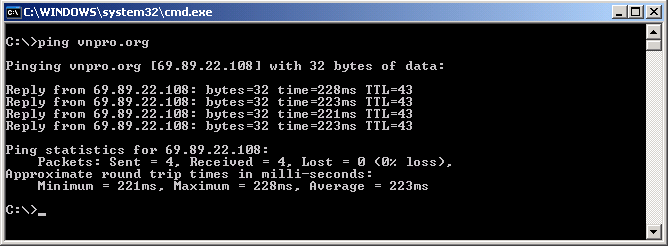
Hình 1.40
ASA(config)# sh xlate
1 in use, 8 most used
Global 195.1.1.0 Local 192.168.1.0
GATEWAY#sh ip nat translations
Pro Inside global Inside local Outside local Outside global
tcp 10.215.219.80:1178 195.1.1.2:1178 208.43.215.134:80 208.43.215.134:80
icmp 10.215.219.80:512 195.1.1.2:512 69.89.22.108:512 69.89.22.108:512
tcp 10.215.219.80:1173 195.1.1.2:1173 220.231.95.20:80 220.231.95.20:80
Link Phần 1 : https://vnpro.vn/thu-vien/chuong-1--tong-quat-hoat-dong-va-cau-hinh-co-ban-thiet-bi-asa-phan-1-3639.html
Link Phần 3 : https://vnpro.vn/thu-vien/chuong-1--tong-quat-hoat-dong-va-cau-hinh-co-ban-thiet-bi-asa-phan-3-3642.html
Thông tin khác
- » CHƯƠNG 1 : TỔNG QUÁT HOẠT ĐỘNG VÀ CẤU HÌNH CƠ BẢN THIẾT BỊ ASA - Phần 1 (17.09.2020)
- » Import CUC Vmware WorkStation lên ESXi- Phần 1 (16.09.2020)
- » Import CUC Vmware WorkStation lên ESXi- Phần 2 (16.09.2020)
- » Cấu hình softphone VTGO-PC-Lite trên PC (thay thế cho CIPC) (15.09.2020)
- » Import CUCM Vmware WorkStation lên ESXi (15.09.2020)
- » Import CUPS Vmware WorkStation lên ESXi (15.09.2020)
- » LAB CUCM. Cấu hình tương tác với CUC trên CUCM - Phần 1 (14.09.2020)
- » LAB CUCM. Cấu hình tương tác với CUC trên CUCM - Phần 2 (14.09.2020)





